If you haven’t heard. FLAME, is a new cyber-security breaching tool or virus that is on the loose in particular regions in Middle-East and according to some sources-Europe.
Well, after hearing this, I was curious enough to dig a bit into this news. Here, I am compiling this article with references from websites BBC, Times of India, Telegraph and Yahoo news.
According to the sources, it was Russian security firm- Kaspersky Labs that first told the BBC that they believed that a new malware known as Flame, had been operating on machines in the Middle-East since August 2010.
The company said that it believed the attack was state-sponsored. But they could never be sure of its exact origins. Still they were sure enough that Flame was one of the most complex threats ever discovered. Research into the attack was carried out in conjunction with the UN's International Telecommunication Union.
They had also been investigating another malware threat, known as Wiper, which was reportedly deleting data on machines in western Asia. In the past, targeted malware - such as Stuxnet - had targeted nuclear infrastructure in Iran. Others like Duqu have sought to infiltrate networks in order to steal data.
This new threat appears not to cause any/much physical damage, but they are designed to collect huge amounts of sensitive information according to Kaspersky.
They say that once the system is infected, Flame begins its unleashing its complex set of operations, including sniffing the network traffic, taking screenshots, recording audio conversations, intercepting the keyboard, and so on.
Kaspersky also said that more than 600 specific targets were hit, ranging from individuals, businesses, academic institutions and government systems.
Iran's National Computer Emergency Response Team (CERT) had posted a security alert stating that it believed Flame was responsible for recent incidents of mass data loss in the country.
The malware code is 20MB in size, which makes it some 20 times larger than the 1MB Stuxnet virus. Researchers say that it could take several years to analyse.
But news also state that ‘Flame’ is not designed to steal money from bank accounts. It is different from simple hacking tools and malware used by the hacktivists. So, that now excludes cybercriminals and hacktivists.
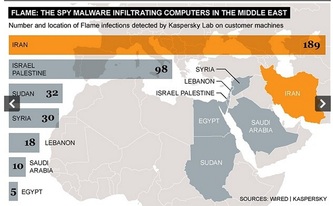
Countries affected by the attack are Middle-Eastern- Iran, Israel, Sudan, Syria, Lebanon, Saudi Arabia and Egypt.
The malware is reportedly also capable of recording audio via microphone, before compressing it and sending it back to the attacker. It is also able to take screenshots of on-screen activity, automatically detecting when interesting programs - such as email or instant messaging - were open.
Kaspersky first recorded Flame in August 2010, although they say that it may have been operating even earlier.
Unlike Stuxnet, Flame is designed to steal almost anything they can get their hands on. And that is what makes it different and dangerous. The entire thing is sophisticated and once the initial Flame malware has infected a machine, additional modules can be added to perform specific tasks - almost in the same manner as adding apps to a smartphone. So beware!!!
According to the sources, it was Russian security firm- Kaspersky Labs that first told the BBC that they believed that a new malware known as Flame, had been operating on machines in the Middle-East since August 2010.
The company said that it believed the attack was state-sponsored. But they could never be sure of its exact origins. Still they were sure enough that Flame was one of the most complex threats ever discovered. Research into the attack was carried out in conjunction with the UN's International Telecommunication Union.
They had also been investigating another malware threat, known as Wiper, which was reportedly deleting data on machines in western Asia. In the past, targeted malware - such as Stuxnet - had targeted nuclear infrastructure in Iran. Others like Duqu have sought to infiltrate networks in order to steal data.
This new threat appears not to cause any/much physical damage, but they are designed to collect huge amounts of sensitive information according to Kaspersky.
They say that once the system is infected, Flame begins its unleashing its complex set of operations, including sniffing the network traffic, taking screenshots, recording audio conversations, intercepting the keyboard, and so on.
Kaspersky also said that more than 600 specific targets were hit, ranging from individuals, businesses, academic institutions and government systems.
Iran's National Computer Emergency Response Team (CERT) had posted a security alert stating that it believed Flame was responsible for recent incidents of mass data loss in the country.
The malware code is 20MB in size, which makes it some 20 times larger than the 1MB Stuxnet virus. Researchers say that it could take several years to analyse.
But news also state that ‘Flame’ is not designed to steal money from bank accounts. It is different from simple hacking tools and malware used by the hacktivists. So, that now excludes cybercriminals and hacktivists.
Countries affected by the attack are Middle-Eastern- Iran, Israel, Sudan, Syria, Lebanon, Saudi Arabia and Egypt.
The malware is reportedly also capable of recording audio via microphone, before compressing it and sending it back to the attacker. It is also able to take screenshots of on-screen activity, automatically detecting when interesting programs - such as email or instant messaging - were open.
Kaspersky first recorded Flame in August 2010, although they say that it may have been operating even earlier.
Unlike Stuxnet, Flame is designed to steal almost anything they can get their hands on. And that is what makes it different and dangerous. The entire thing is sophisticated and once the initial Flame malware has infected a machine, additional modules can be added to perform specific tasks - almost in the same manner as adding apps to a smartphone. So beware!!!

 RSS Feed
RSS Feed

